Algorithms
When dealing with system design questions such as designing a rate limiting system, a sharding system, or a global location service, candidate can use some of the following system design algorithms during the interview.
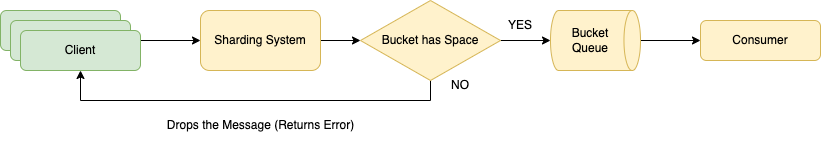
Leaky Bucket Algorithms
Use-case: Rate Limiting Systems
Process
- a client send a message to the server
- the server uses an sharding algorithms to find the corresponding bucket for the message
- the server tries to append the message to the bucket - a local message queue
- if the queue is full (i.e. has
bucket_sizemessage in the queue already), then drop the message - if the queue has space, append the message to the end of the queue
- if the queue is full (i.e. has
- the consumer will pull message from the queue with a rate of
drain_rate - the consumer process the message
Parameters
bucket_size: the maximum amount of messages can be stored in each bucketdrain_rate: the speed that the message is been consumed from the bucket
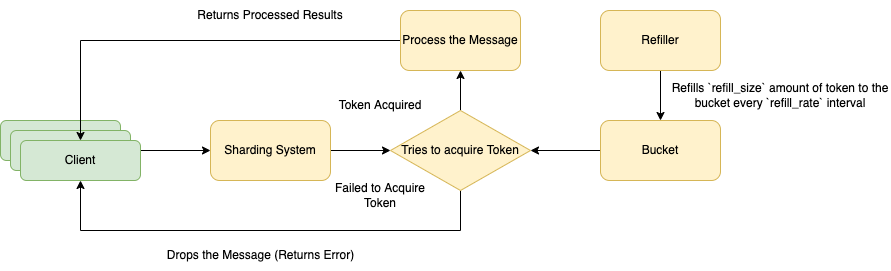
Token Bucket Algorithms
Use-case: Rate Limiting System
Process
- a client send a message to the server
- the server uses an sharding algorithms to find the corresponding bucket for the message
- the server tries to acquire a token from the bucket
- if a token is acquired, the request is processed
- if no token exist in the bucket, the request is dropped
- the bucket receive a refill of
refill_sizeamount of token each for eachrefill_rateinterval - the amount of token can be stored in the bucket is limited by the
bucket_size
Parameters
bucket_size: the maximum amount of token can be stored in each bucketrefill_size: the amount of tokenrefill_rate: the time interval between each refill
Alteration
- token per request: for each token, the system can process one message. if there are
nmessage, then it would requiresntoken from the bucket for all the message to be processed. - token per bytes: for each token, the system can process
xbyte of message. if there arenmessage each withssize, then it would requiresCEIL(x / s) * ntokens from the bucket for all message to be processed.